How Can Digital Assets Create an Impact in Safeguarding the Devices?

Digital assets belonging to a corporation hold the same value as physical assets and properties. You would use platforms like asset management systems to ensure that they’re working at their best condition, but also to keep attackers out. However, as time goes on, hackers and threats become more sophisticated, so it’s important for us to stay ahead of their tactics.
In this article, we’ll delve deeper into finding out how digital assets can play a big role in safeguarding devices for operational technology.
What Is a Digital Asset and What Are Examples of It?
Before we head over to the impact created by digital assets in protecting your devices. Let’s first understand what a digital asset is. So, digital assets can range from digitalized goods, and digitalized components to business assets that are found on the internet. Any content that the company uploads online is considered a digital asset, and you would use an OT asset inventory to ensure everything is accounted for.
With that said, here are some examples of digital assets:
- Websites and blog entries: Your website and its many blog entries are digital assets that are copyright-protectable.
- Ideas and SOPs: Did your team concoct unique concepts or steps in performing business tasks and posted them online? These ideas and SOPs have a lot of value and are thus considered digital assets.
Let’s use an example: Your company created guidelines on how to use a security asset management platform. Then your company posts a published blog post about it. Not only is it copyright-protectable but it is also your organization’s intellectual property.
- Client and customer registries: Your organization may maintain lists of clients and customers. These lists get used for sending newsletters and corporate news or updates. This digital asset will need a lot of security since every competitor is itching to get their hands on client and customer lists.
- Design elements such as logos and banners: Graphics such as your group’s logos and banners are intellectual property and need protection as they have value.
What Practices Can Make Digital Assets Protect Devices?
If you want your OT environment and its assets to be well-protected, you’ll need to utilize specific practices. By using the methods we’ll cover; your assets will be key in making your digital devices less vulnerable to attacks. Your hackers or attackers could end up giving up in trying to break into your system.
Here are some practices that you can use to ensure both digital assets and devices are well-defended:
1. Utilizing Multi-Factor Authentication

(Image Source: Pixabay)
The first line of defense for OT environments is implementing a multi-layered authentication system. Configure it with your security asset management system so that attackers won’t enter your system and devices. Examples of multi-factor authentication methods include security questions, facial recognition, and fingerprint scans.
2. Managing User Authentication
The person responsible for managing security asset management should control user permissions within the system. Give users only specific permits for what tasks they’re going to perform within your organization’s system. If you end up giving full access to everyone, this may result in unforeseen consequences.
Also, a quick tip – you may create groups of users to simplify the process of assigning permits and managing the users.
3. Form a File-Level Protection
Another effective method for safeguarding devices is implementing clearance levels. Clearance levels are a tiered system of access wherein a user of this level can only access specific content. It’s a good way to keep unauthorized access out of critical organizational files and key digital devices. Let’s use an example of this practice:
- For instance, you are managing the security system for your organization’s OT asset inventory and users are asking for access to these files. Let’s say, an administrative team member is requesting access to critical files. You would want to check with them if the higher-ups gave them that task. If so, you can provide them with clearance to access the folder containing the requested files and assets.
4. Protect Your Organization’s Branches and Streams
You must also control who is allowed to apply changes in digital assets and devices. For example, you can grant permission only to specific members and roles related to an assigned folder. Let’s say the Sales folder for instance, you’ll only authorize the members of the Sales team to access this area where they can edit and modify files related to their department.
As for the critical files and assets, you can authorize key members in the Administrative team to manage and modify them if necessary.
5. Encrypt Your Assets and Devices
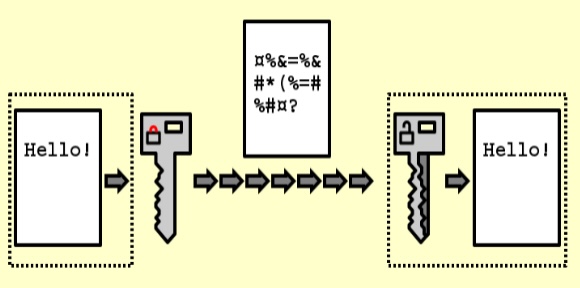
(Image Source: Wikimedia Commons)
Encrypt your organization’s files to the highest extent possible, both when stored in the repository and during transfer. The reasoning behind this is that assets and devices could be cracked open by an attacker in the process. Thus, it allows them to take the information and steal them away. If you encrypt your assets, you prevent the hackers from cracking them open.
6. Record All User Activity
Recording and tracking all user activities is crucial to ensure the security of your company’s OT asset inventory. Records can provide developers and cybersecurity with logs of past activities and see if there are any suspicious happenings inside the asset inventory.
To ensure that suspicious activities are curbed, the inventory could use audit trails to spot any risky behavior. Audit trails will analyze the behavior of each user to narrow down on users that are suspected of doing dangerous activity. The use of audit trails is very useful for counteracting any potential inside jobs.
7. Employ a Single but Secure Repository
While storing items in multiple categorized repositories may seem acceptable, it can be more of a disadvantage. Having multiple storage areas can become a potential angle of attack on your organization. What you can do instead is to place all assets and digital devices inside one organized and secured repository.
- Let’s use an example for this case: Your organization has a lot of files with various categories. Before, they were in many storage areas which can be hectic to manage. Then your organization compiled all assets and devices and stored them in one central storage, with categorized folders (e.g. encrypted cloud storage). But, you will need to tweak the access settings for each category to ensure the right people are accessing it.
- An additional tip, try creating a backup of each key asset. They’ll come in handy if ever system maintenance or a shutdown happens.
Well-Secured Assets Make for a Secured Device
Securing your digital assets will contribute to a well-defended digital device. By using all the practices above with a security asset manager, you can control who can go in and out of critical areas in the system. Aside from that, you also ensure that no attacker will be able to touch your organization’s most treasured tools and devices.
FAQs
1. What is an inside job?
Inside jobs are attacks that occur within the organization. One of the team members could be an accomplice of an outside entity. The team member could lower the security of each asset and may cause huge damage if it’s not detected early. Fortunately, inside jobs can be traced through audit trails which we’ve covered earlier.
2. Why is file-level protection necessary?
Some organization documents are highly confidential and must not be leaked to the public. These documents could contain plans and strategies that are crucial to an organization’s success. If these files get leaked out, the competition could get a hold of them or attackers can use the information to damage your organization.
3. Why is multi-factor authentication a necessity in OT systems?
Multi-factor authentications are necessary to ensure the legitimacy of an individual’s identity. It also prevents impersonators from accessing your organization’s system and key assets.




























